Transform your career by learning how hacking really works
Stop leaning on Metasploit and Nessus. Understand how exploits actually work, and how to stop them.
Hands-on Courses • Active Community • Hacking Challenges
Join now and get instant access to our FREE Hacking Challenge
Meet Your Instructor

Ed, also known as Low Level, is a low level programmer, security engineer, and software security researcher with over 10 years of experience. On YouTube, he has over 1,000,000 subscribers where he teaches the internet how to harness the lowest levels of computing.
Here on StackSmash, he'll teach you the fundamentals to understand how real-world exploits work (and how to stop them).
Available Courses
Master the skills you need to become a software security expert. Each course is designed to take you from beginner to advanced.








Ready For More?
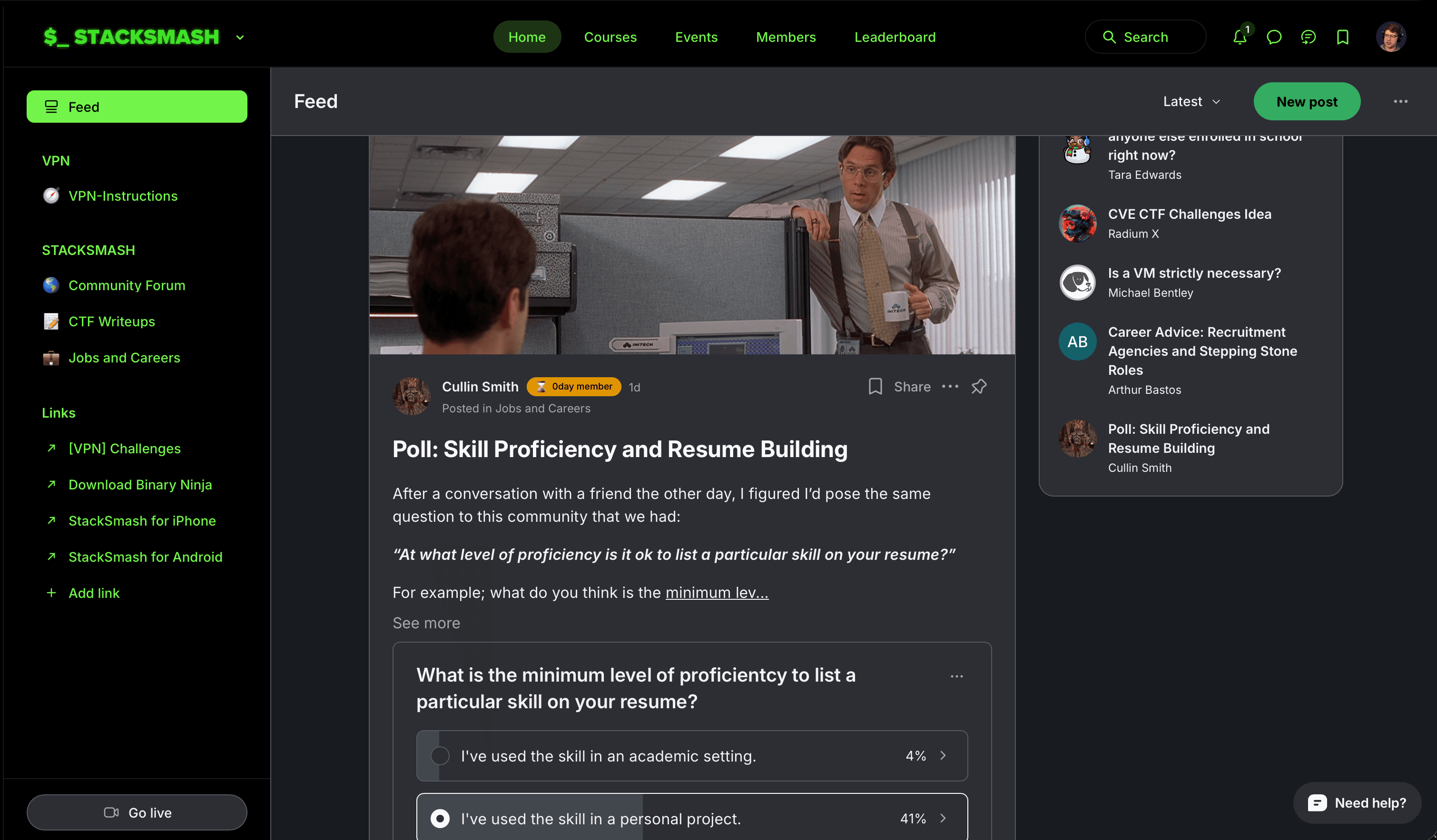
Active Community
Join a group of peers that are trying to accomplish the same goal as you, helping along the way.
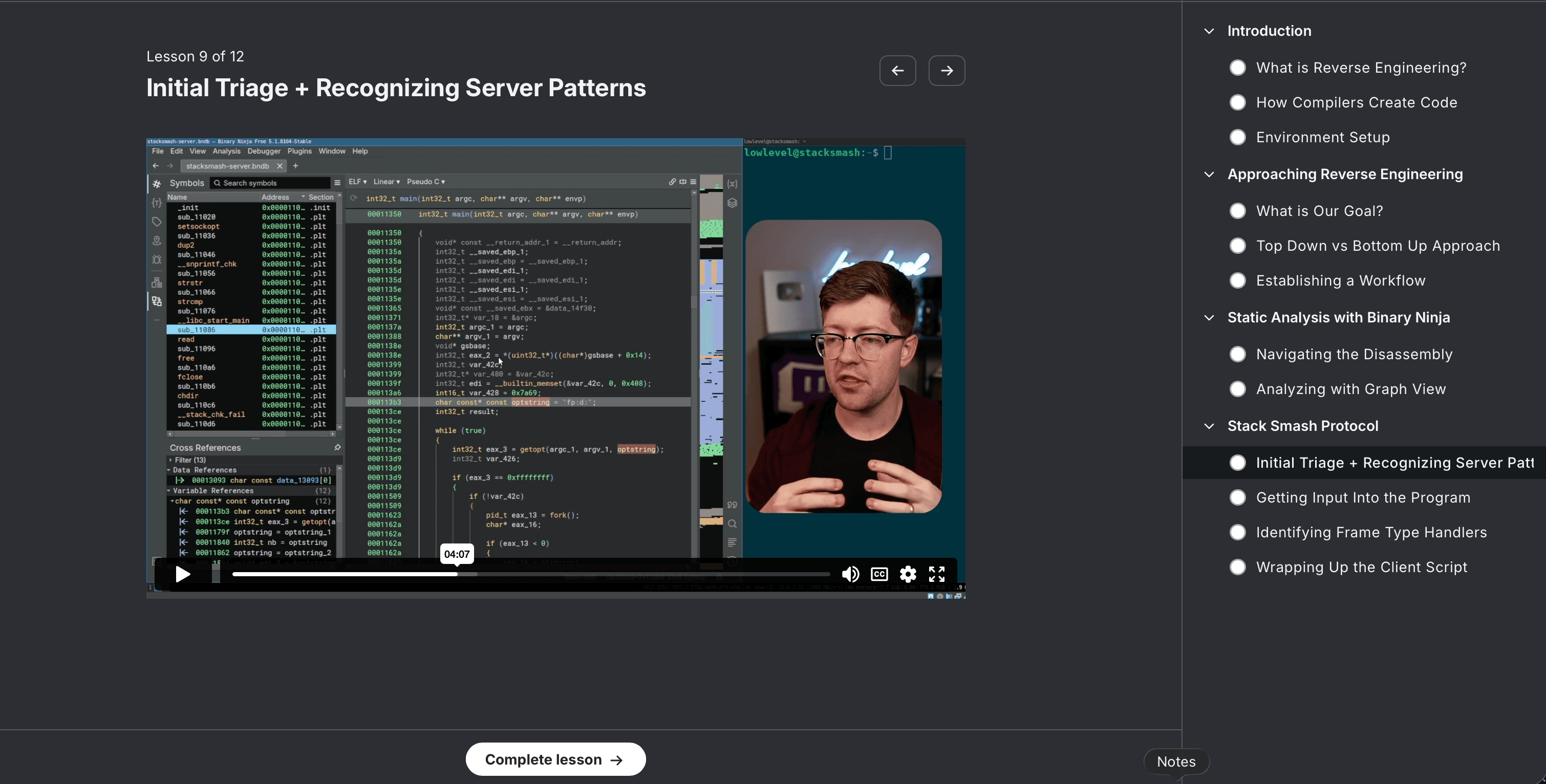
Hacking Courses
Learn low level computing, how to program in C, write exploits in Python, reverse engineer software, and fuzz software.
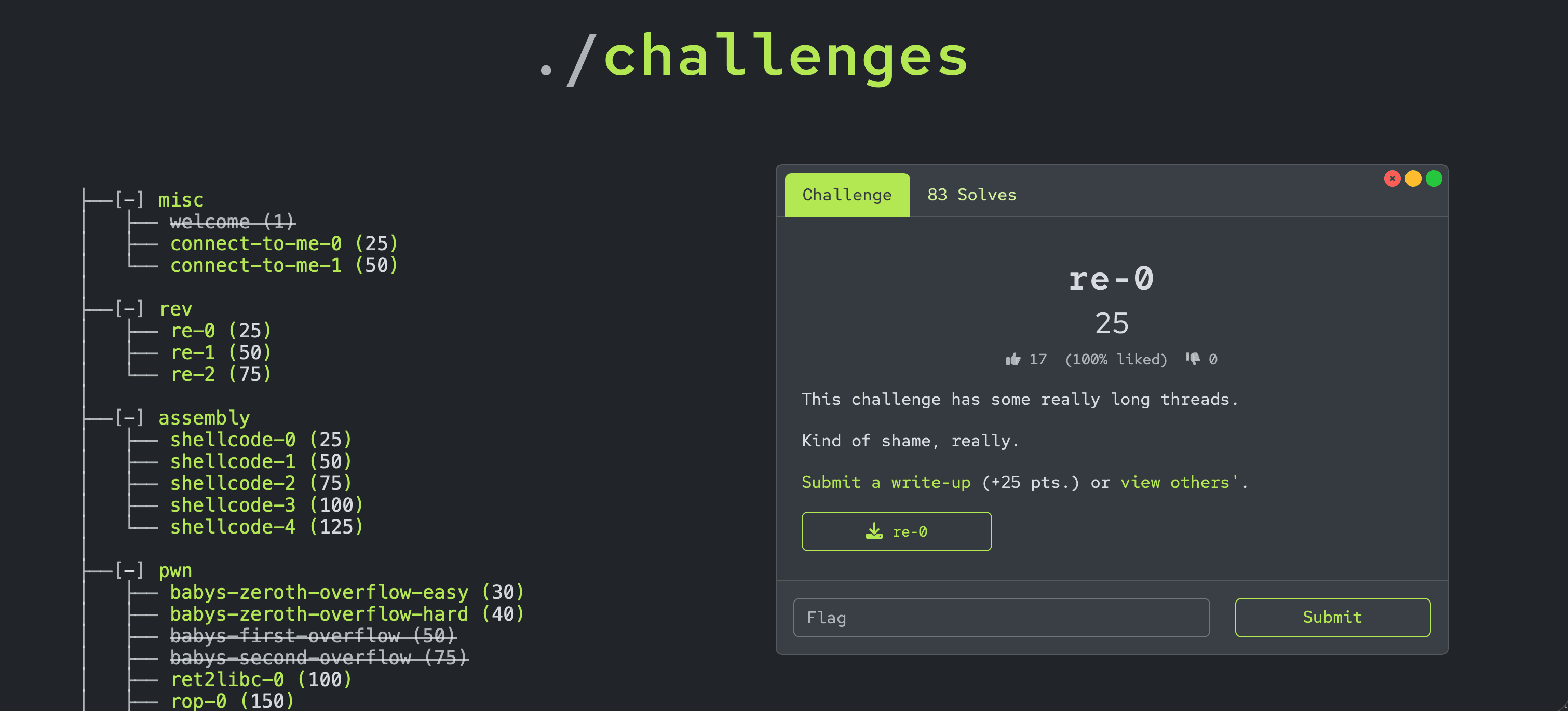
CTF Challenges
Compete in CTF Challenges with the community to gain experience and level up your skills.
What Members Are Saying
Weekly Office Hours
Get your questions answered in real-time during our weekly Q&A sessions
Weekly Q&A Sessions
Join us every week for live Q&A calls where you can ask questions, get help with challenges, and learn from the community.
Direct Access to Experts
Get personalized guidance from experienced security professionals who understand your journey and can help you overcome obstacles.
Community Learning
Learn from questions others are asking. Every session is an opportunity to discover new techniques and perspectives.
Learning is easier with a community
Maybe this is you:
There have been dozens of times during my hacking journey where I've been stuck, trying to figure out a complicated concept.
Eventually a little lightbulb goes off and 'oh, I get it now!'
Every one of these moments can be accelerated with a community
Every one of those moments makes you a better security professional
Frequently Asked Questions
Everything you need to know about StackSmash